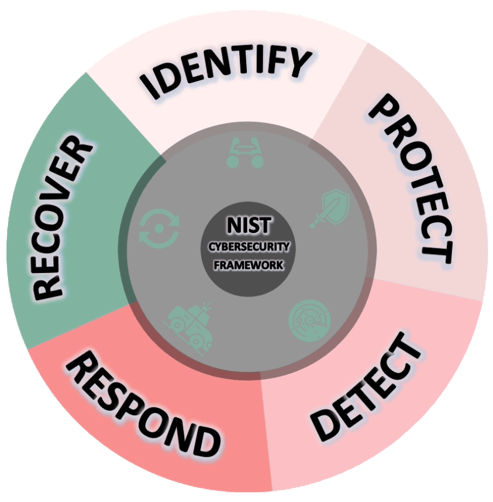
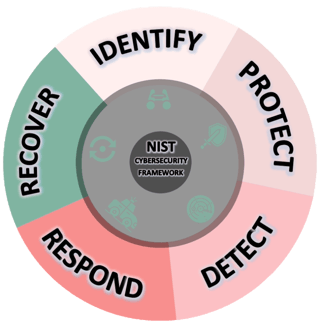
IDENTIFY
We lay the foundation by comprehensively understanding and cataloging your assets, vulnerabilities, and potential risks. This step serves as the bedrock for a resilient cybersecurity strategy.
Cyber Risk Assessments
Penetration Testing Red/Blue/Purple Teaming (Continuous or Ad-Hoc)
Compliance Gap Assessments (CMMC, HIPPA, ISO, PCI Rediness)
Risk Management & Cybersecurity Strategy
CISO as a Service
We implement proactive measures to safeguard critical assets and data through robust access controls, encryption, training, and secure architectures.
Mock Scenario Exercises
Incident Response
Continuity of Operations
Table-Top
Security Architecture & Engineering
Zero-Trust Architecture
We establish mechanisms to promptly identify cybersecurity events through continuous monitoring, anomaly detection, and incident response protocols.
Compromise Assessments
Managed Security Service Provider (MSSP)
Continuous Monitoring
Awareness
We develop and implement a robust response plan to address incidents efficiently and mitigate their impact on operations, customers, and stakeholders.
Incident Response
Forensics
Malware Reverse Engineering
Internal/External COMM's
We build strategies for quick recovery and restoration of capabilities post-incident, ensuring minimal disruption and swift restoration.
Remediation Assistance
Develop Lessons Learned Briefs
Action Plans
PROTECT
DETECT
RESPOND
RECOVER
At Upward, we're dedicated to partnering with organizations on their journey towards robust cybersecurity. Our team of experts specializes in NIST Framework implementation, providing tailored strategies, comprehensive assessments, and ongoing support to ensure your organization not only meets but exceeds cybersecurity standards.
NIST Framework
Take your Security Posture

info@upwardcyber.com
415 Boston Post Rd
STE 3-2130
Milford, CT 06460


© 2025 Upward, a Cybersecurity and Risk Management company.
Resources
Careers